EXIF Data Fact-Checking for Journalists: A Verification Guide
In today's digital media landscape, a single manipulated image can go viral and shape public opinion before the truth emerges. When the Associated Press revealed that viral images from a political rally were actually from different events, the key evidence was hidden in plain sight—within the EXIF data. This metadata, embedded in every photo, is a powerful tool against misinformation.
How can you, as a journalist, harness this data to protect your publication's credibility?
This article reveals how you can use this often-overlooked information to verify photo authenticity, detect digital manipulation, and maintain trust in an era of sophisticated fakes. With the right techniques and a secure tool, fact-checking images becomes a manageable part of your workflow. For a quick and private analysis, you can view EXIF data directly in your browser without uploading any files.

Understanding EXIF Data for Photo Verification
Before you can use EXIF data for fact-checking, it's crucial to understand what it is and what it isn't. EXIF stands for Exchangeable Image File Format. It's a standard that defines formats for images, sounds, and tags used by digital cameras and other systems that record images and sound files. Think of it as a photo's digital fingerprint.
This metadata provides a rich history of the image, offering clues that are invaluable for verification. By learning to read these clues, journalists can add a powerful layer of defense against doctored content.
What EXIF Data Reveals About Image Origins
Every time a digital camera or smartphone takes a picture, it saves a wealth of information directly into the image file. This data can tell you a story about how, when, and where the photo was taken.
Key pieces of information often include:
- Camera Details: The make and model of the camera or phone (e.g., Canon EOS R5, Apple iPhone 14 Pro).
- Time and Date: The exact date and time the photo was captured, down to the second.
- Camera Settings: Technical details like shutter speed, aperture, ISO, and focal length.
- GPS Coordinates: If enabled, the precise latitude and longitude where the photo was taken.
- Software Information: The software used to process or edit the image (e.g., Adobe Photoshop, Lightroom).
This information provides a baseline for confirming a photo's context. If a photo claims to be from a protest in Paris today, but its EXIF data shows it was taken two years ago in Berlin, you have an immediate red flag.
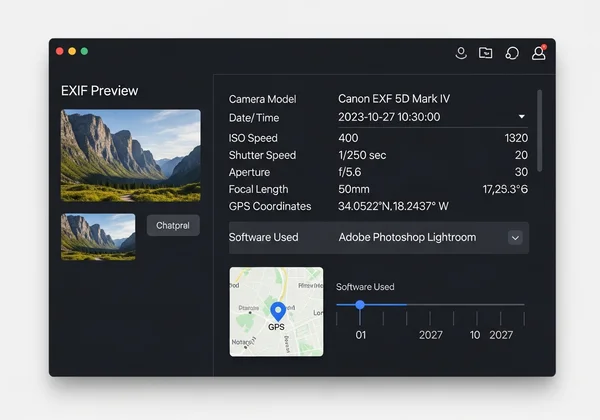
Critical EXIF Tags for Authenticity Verification
While there are hundreds of possible EXIF tags, a few are particularly vital for journalistic fact-checking. When you inspect an image, focus on these critical fields to quickly assess its authenticity.
DateTimeOriginal: This is the moment the shutter was pressed. It is one of the most reliable indicators of when an event occurred. Cross-reference this timestamp with known event timelines.GPSLatitude/GPSLongitude: These tags pinpoint the photo's location. This is essential for verifying claims about where an image was captured. You can use these coordinates in mapping software to see the exact spot.Make/Model: Knowing the camera used can help you identify inconsistencies. For example, if a photo purports to be from the 1990s but the camera model was released in 2015, the story doesn't add up.Software: This tag often shows if an image has been processed with editing software. The presence of "Adobe Photoshop" doesn't automatically mean a photo is fake, but it signals that the image is no longer in its original state and requires closer inspection.
To check these tags without compromising source material, a secure image metadata viewer is an indispensable tool.
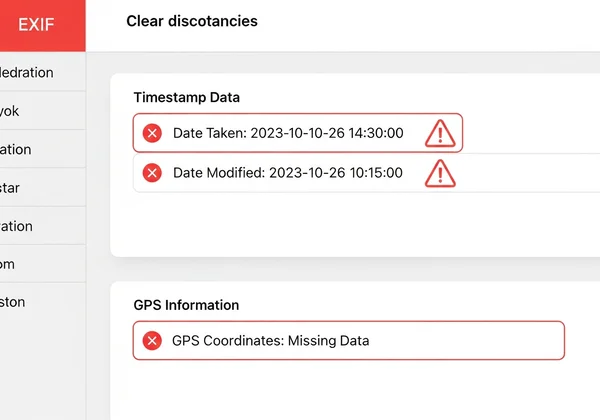
Spotting Signs of Image Manipulation in Metadata
Manipulators often get sloppy and leave behind digital breadcrumbs in the metadata. The absence of data can be just as telling as its presence.
Here are common signs of manipulation to look for:
-
Missing EXIF Data: If a photo from a supposedly credible source has no EXIF data at all, be suspicious. Most social media platforms strip metadata for privacy, but images sent directly from a source should contain it. The absence might mean it was intentionally removed.
-
Conflicting Timestamps: Some EXIF records contain multiple timestamps, such as
DateTimeOriginal,CreateDate, andModifyDate. If these dates are wildly different, it could indicate editing or re-saving of the file. -
Inconsistent Camera Settings: An experienced photographer might notice if the EXIF settings (like a slow shutter speed) don't match the visual content (a perfectly sharp image of a fast-moving object).
-
Suspicious Software Tag: A simple "Photos App" software tag might be normal, but a tag showing advanced editing software on a photo claiming to be raw and unedited is a major warning sign.
Step-by-Step EXIF Verification Process
Having the right knowledge is only half the battle. Integrating EXIF analysis into your daily workflow requires a systematic process. This ensures you can quickly and reliably check images, especially when facing tight deadlines.
This step-by-step approach will help you build a routine for photo verification that strengthens your reporting and protects your outlet's reputation.
Initial Assessment: When to Suspect Image Authenticity Issues
Not every image requires a deep forensic analysis. Your journalistic intuition is the first line of defense. Learn to recognize situations that carry a higher risk of misinformation.
Trigger an EXIF check when:
- The image comes from an unverified or anonymous source.
- The photo depicts a highly emotional or controversial event.
- The visual content seems too perfect, too shocking, or out of context.
- The image is circulating rapidly on social media without a clear original source.
- You receive a "tip" that seems designed to confirm a specific narrative.
In these cases, pausing to conduct a quick metadata check can prevent you from amplifying a falsehood. It’s a small step that can have a huge impact.
Using Privacy-Focused Tools for Safe Analysis
When working with sensitive images, especially from vulnerable sources, privacy is paramount. Uploading a photo to a random online tool can expose the file, its metadata, and your IP address to a third party. This could compromise your source and your investigation.
This is why choosing a privacy-first tool is non-negotiable. A client-side EXIF reader processes the image entirely within your web browser. The photo never leaves your computer, ensuring complete confidentiality.
With a tool like ExifReader.org, you can safely drag and drop any image file and instantly see its metadata without any upload. This zero-risk approach is essential for modern newsrooms that handle sensitive information.
Cross-Referencing Metadata with Image Content
Metadata alone is not absolute proof. It must be analyzed in conjunction with the visual information in the photo and external facts. This holistic approach is the cornerstone of effective verification.
For example, if the EXIF data provides GPS coordinates, use a map service to examine that location. Does the street view match the background in the photo? If the timestamp points to a specific time of day, check the shadows and lighting in the image. Do they correspond to the sun's position at that time and location?
Also, cross-reference the DateTimeOriginal with news reports and social media posts from that day. This process of connecting the metadata dots with real-world context turns a simple data readout into compelling evidence.
Real-World Case Studies in Photo Verification
Theory is useful, but seeing EXIF fact-checking in action demonstrates its true power. Examining past successes and failures in photojournalism provides valuable lessons for today's media professionals. These cases highlight how a few lines of metadata can uncover the truth or, when ignored, allow misinformation to thrive.
Breaking the "Syrian Refugee Crisis" Misinformation
During the height of the Syrian refugee crisis, a powerful photo circulated showing a young boy sleeping between two graves, supposedly his parents. The image went viral, evoking strong emotional responses worldwide.
However, the photographer who took the shot came forward to debunk the story. He explained the photo was part of a conceptual art project and the boy was his nephew, not an orphan. A quick check of the photo's metadata would have revealed the photographer's name and copyright information under IPTC tags, another form of metadata. This would have allowed journalists to contact the creator directly and verify the context before publishing, preventing the spread of a false narrative.
How EXIF Data Exposed Location Scams in News Coverage
In another instance, a freelance journalist submitted photos of a purported conflict zone to a news agency. The images were dramatic and seemed to confirm reports of fighting in a remote village. The agency was about to run the story.
However, a skeptical photo editor decided to check the EXIF data first. The GPS tags embedded in the images told a different story. The coordinates placed the photographer not in a war-torn village, but hundreds of miles away in a different country, near a known film set. The EXIF data single-handedly prevented the publication of a fabricated story and exposed a fraudulent source.
Technical Limitations: When EXIF Data Isn't Enough
It is crucial to be honest about the limits of EXIF data. Metadata can be altered or stripped entirely. A determined manipulator can use specialized software to change timestamps, remove GPS coordinates, or even implant fake information.
Additionally, major social media platforms such as Facebook, X (formerly Twitter), and Instagram automatically strip most EXIF data from uploaded images. They do this to protect user privacy. When you find an image on these platforms, the original metadata has probably already been removed.
In these cases, EXIF analysis is not the end of the story. It should be one tool in a broader verification toolkit that includes reverse image searching, source vetting, and analysis of visual clues within the photo itself.
Building a Photo Verification Protocol for Your Newsroom
As journalists navigate today's complex media landscape, EXIF data serves as an essential ally in distinguishing fact from fiction. It provides an objective, data-driven foundation for verifying the authenticity of an image. By understanding what metadata reveals, spotting signs of manipulation, and using safe tools, you can protect yourself and your audience from falsehoods.
Here's what you should remember:
- Always Be Skeptical: Treat images from unverified sources with suspicion and make metadata analysis a default step.
- Prioritize Privacy: Use client-side tools that process images in your browser to protect your sources and your investigation.
- Cross-Reference Everything: Combine metadata clues with visual analysis and external facts for a complete picture.
Adopting a formal photo verification protocol is no longer optional—it's essential for maintaining credibility. Start today by making a secure, private metadata analysis tool part of your workflow. For instant and safe analysis, try our free tool now.
The Takeaway
Can manipulated images still have accurate EXIF data?
Yes, it's possible. An editor could perform minor color correction or cropping, which would be noted in the Software tag, while leaving the original timestamp and GPS data intact. This is why it's crucial to look at the whole picture and not rely on a single data point. The presence of an editing software tag should prompt a closer look, not an immediate dismissal.
How do I verify EXIF data hasn't been altered?
There is no foolproof way to guarantee EXIF data is 100% original, as sophisticated tools can rewrite it. However, you can look for inconsistencies. For example, if a photo's DateTimeOriginal tag is from 2023, but the Make and Model tags point to a camera released in 1999, something is wrong. Using a reliable online EXIF reader helps you spot these conflicts easily.
Are there ethical considerations when analyzing photo metadata?
Absolutely. While EXIF data is a powerful tool for fact-checking, it can also contain sensitive information, especially GPS coordinates that might reveal a source's home or a victim's location. As a journalist, you have an ethical duty to protect this information. Always use secure, privacy-focused tools that do not upload or store the images you analyze, and never publish sensitive metadata without a compelling public interest and the consent of those involved.